Transitioning to SAP S/4HANA is pivotal for organizations modernizing their ERP systems. However, integrating legacy applications into the SAP Fiori launchpad introduces unique challenges, particularly around authorization setup. Missteps in this critical area can lead to security vulnerabilities, productivity loss, and compliance risks.
Standard Authorization Mistakes and Their Impacts
1. Improper Role Assignment
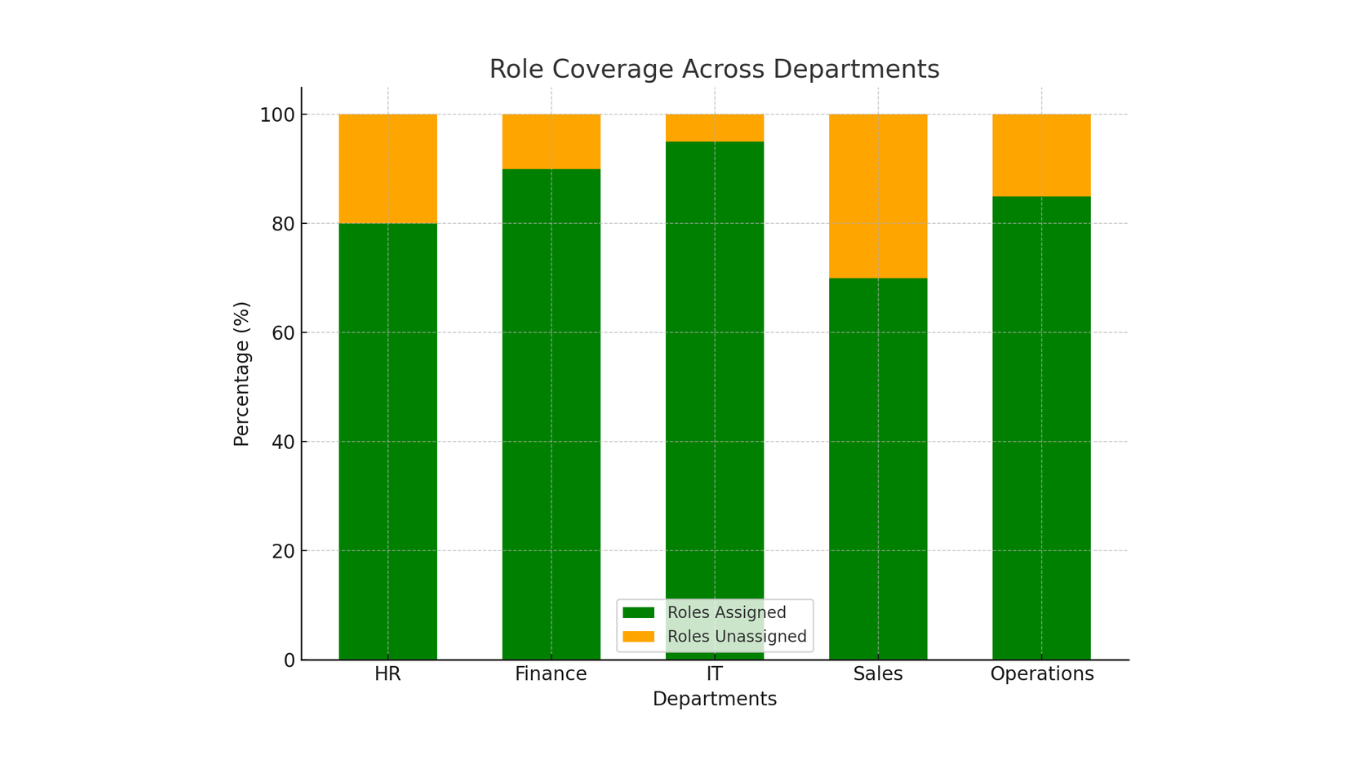
Mistake: Users are often assigned incorrect roles due to misunderstandings about which roles provide access to specific legacy applications.
Implications:
- Security Risks: Unauthorized access can lead to data breaches.
- Operational Inefficiencies: Insufficient access hampers productivity.
Advice: Conduct a thorough role analysis to map job functions to necessary permissions. Leverage SAP's role templates but customize them to your organization's needs.
2. Inadequate Configuration of Catalogs and Groups
Mistake: Neglecting to properly group legacy apps into catalogs and groups aligned with user roles.
Implications:
- Confusion: Users struggle to find relevant applications.
- Administrative Overhead: Complex management of access controls.
Advice: Adopt a structured approach to catalogs and groups. Ensure they mirror your organization's hierarchy and workflows for a seamless user experience.
3. Failure to Update Legacy App Authorizations Post-Migration
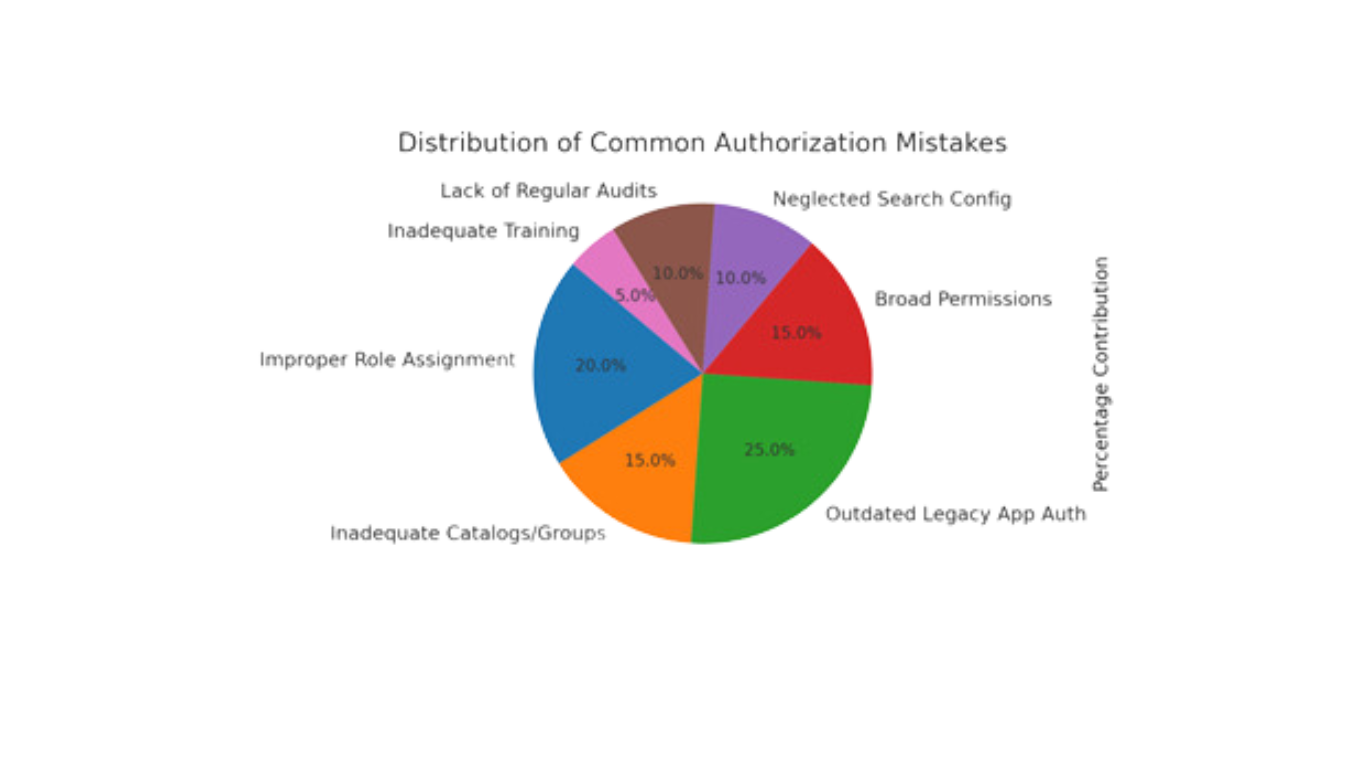
Mistake: Overlooking the need to update legacy application permissions during migration to SAP S/4HANA.
Implications:
- Data Exposure: Legacy permissions may not align with updated security protocols.
- Compliance Risks: Outdated settings can lead to regulatory penalties.
Advice: Reassess all legacy application authorizations during migration. Align them with current compliance requirements and SAP's best practices.
4. Neglecting Differences Between App Types
Mistake: Treating all app types (transactional, analytical, and object pages) the same.
Implications:
- Restricted Capabilities: Transactional apps may not function correctly.
- Data Overexposure: Sensitive analytical data might be unnecessarily accessible.
Advice: Understand the unique requirements of each app type. Implement fine-grained permissions to address their specific needs.
5. Overly Broad Permissions
Mistake: Granting too permissive roles is often a shortcut to resolving access issues.
Implications:
- Heightened Security Risks: Increases the likelihood of unauthorized actions.
Advice: Follow the Principle of Least Privilege. Begin with minimal permissions and gradually expand as necessary. Avoid using wildcard entries in role configurations.
6. Ignoring Contextual Search Requirements
Mistake: Failing to configure authorizations for SAP Fiori Search, especially for sensitive data.
Implications:
- Data Leakage: Sensitive information may appear in search results.
Advice: Restrict search visibility through tailored authorizations. Regularly test search functionality to ensure sensitive data remains protected.
7. Lack of Regular Reviews and Audits
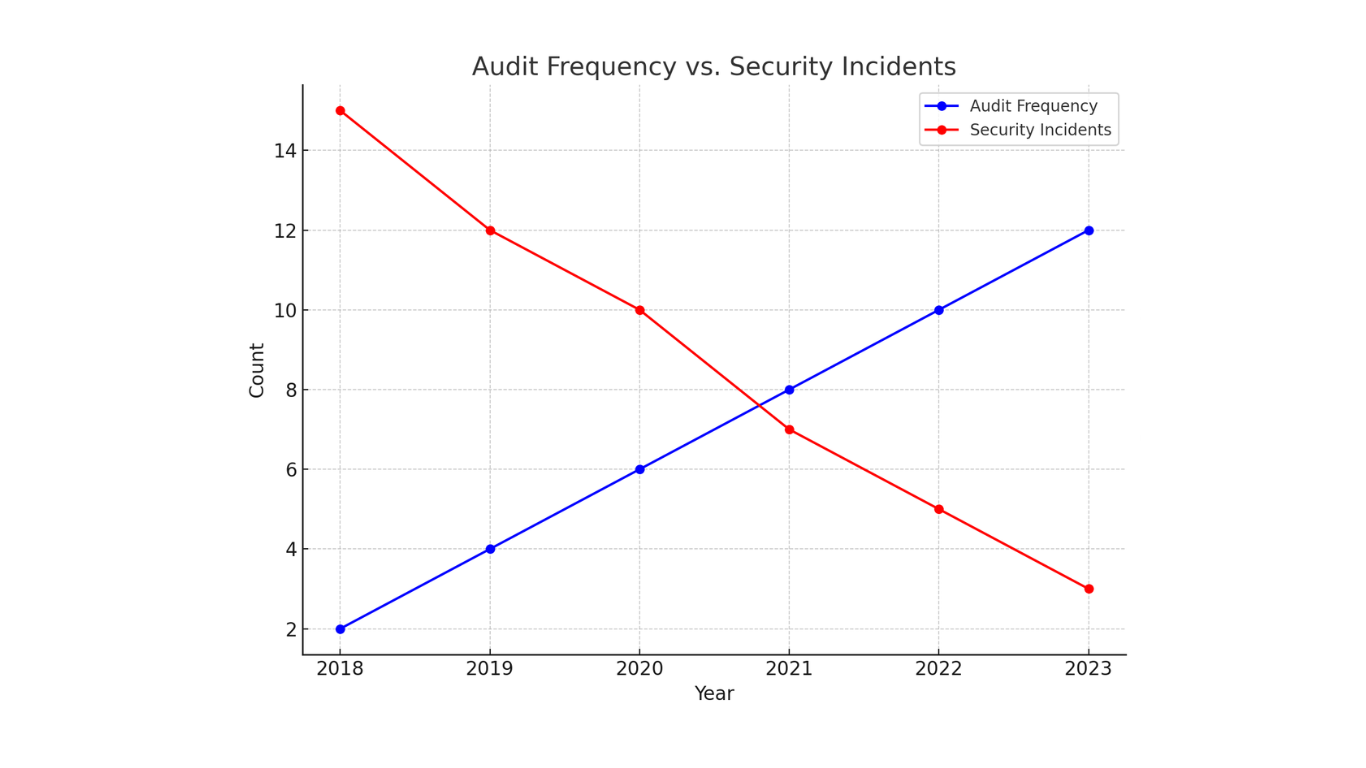
Mistake: Neglecting periodic audits of user access and roles.
Implications:
- Stale Permissions: Users retain access they no longer need.
- Compliance Failures: Increased risk of failing regulatory checks.
Advice: Schedule regular access reviews and leverage SAP tools like Access Control and Audit Logs. Involve cross-functional teams to validate role relevance.
8. Inadequate Documentation and Training
Mistake: Skipping proper documentation and training on the authorization framework.
Implications:
- User Errors: Misconfiguration is due to a lack of understanding.
- Operational Slowdowns: Increased dependency on IT for fixes.
Advice: Develop comprehensive training programs and maintain up-to-date documentation. Empower end-users and administrators with the knowledge to manage their roles effectively.
Encouragement: Strengthening Your SAP Authorization Framework
Securing legacy applications in SAP S/4HANA is not just about compliance—it's about enabling your workforce to perform efficiently while safeguarding sensitive data. By avoiding common pitfalls, you can establish a robust authorization framework that promotes security, productivity, and compliance.
Key Takeaways:
- Be Proactive: Regularly update and audit your authorization settings.
- Think Granular: Avoid broad permissions; tailor roles to user needs.
- Educate: Invest in training and documentation to minimize errors.
By taking these steps, your organization can fully leverage the capabilities of SAP S/4HANA while mitigating risks associated with legacy applications.