You're not alone if you face authorization problems in your SAP S/4HANA Fiori environment. These issues are complex, given the sophisticated nature of the platform and the various components involved. This blog will discuss the five most complicated authorization challenges in SAP S/4HANA Fiori and how to overcome them.
1. Complex Role Mapping and Assignments
One of the most complex challenges in SAP S/4HANA Fiori authorization is managing the role mapping and assignments. Fiori apps rely on a robust system of roles and authorizations, but ensuring that the right roles are assigned to the right users in a manner that reflects their responsibilities can be tricky.
Key Issues:
- Role Inheritance: Many Fiori roles are built on top of standard SAP roles. This inheritance structure can result in unexpected behaviors or conflicting permissions if not carefully managed.
- Segregation of Duties (SoD): Balancing the need for sufficient access with the requirement to maintain Segregation of Duties can lead to complex role configurations.
- Custom Roles: Creating custom roles tightly aligned with specific business processes without violating security protocols adds another layer of complexity.
Solution:
A thorough understanding of SAP's PFCG (Profile Generator) and SU01 (User Maintenance) transactions is essential when defining roles. Check role dependencies and regularly audit and test roles for potential conflicts.
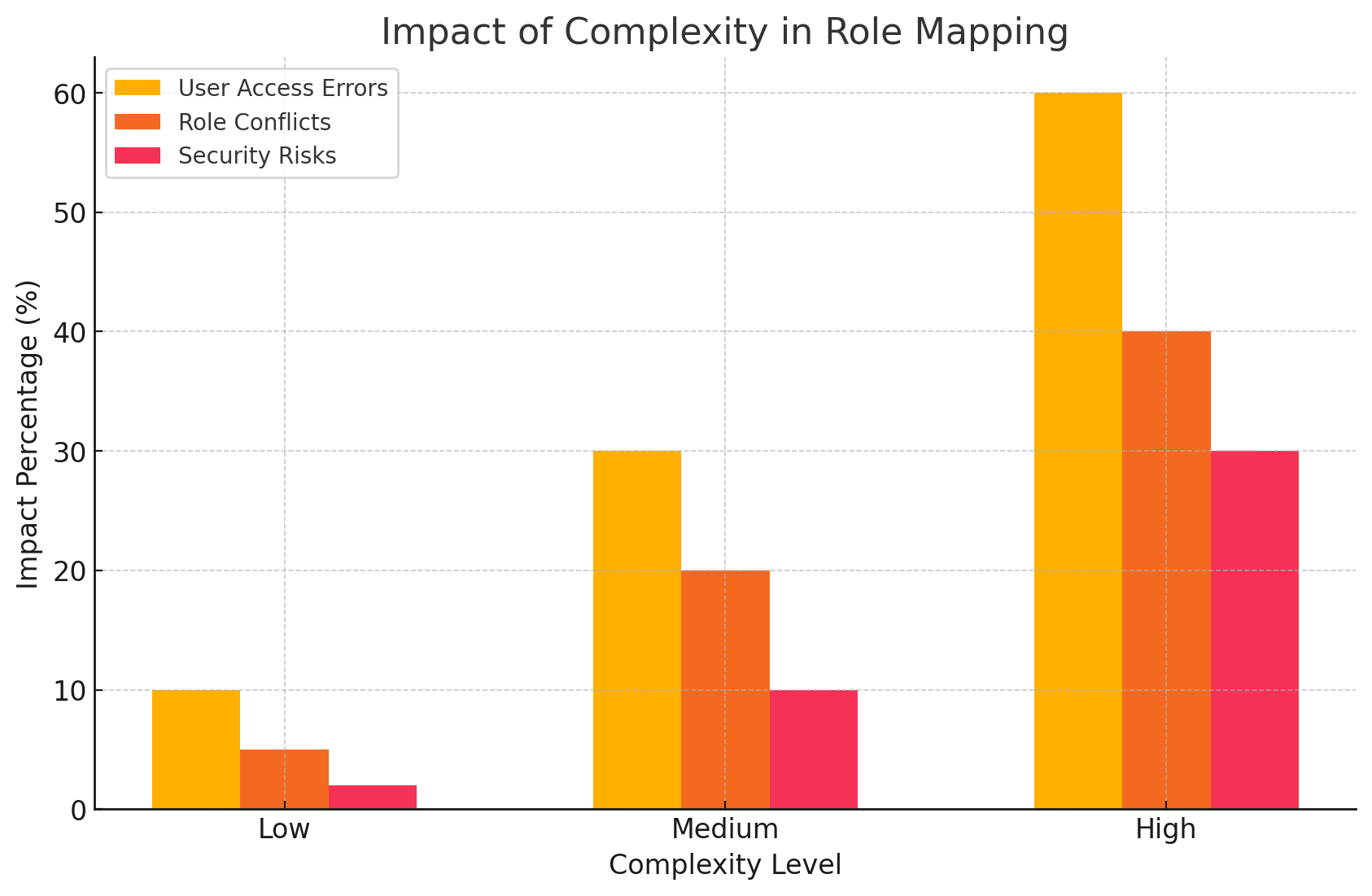
Impact of Complexity in Role Mapping
This bar chart represents the impact of complexity in role mapping, showing the increasing user access errors, role conflicts, and security risks as the complexity of role assignments increases.
2. Authorization Failures Due to Missing or Incorrect OData Services
Fiori apps work by communicating with SAP backend systems through OData services. These services must be activated and configured adequately for seamless functionality. Missing or misconfigured OData services can cause serious authorization issues.
Key Issues:
- Missing OData Services: Often, necessary OData services are not activated in the system, leading to errors when users try to access Fiori apps.
- Backend Configuration Mismatch: If the backend system's authorization checks are not aligned with the Fiori frontend system, access may be denied even if the user has the appropriate roles.
Solution:
Regularly check that all relevant OData services are activated using the transaction /IWFND/MAINT_SERVICE. Ensure that the services are configured correctly on the frontend and backend systems and that users have the appropriate authorizations for these services.
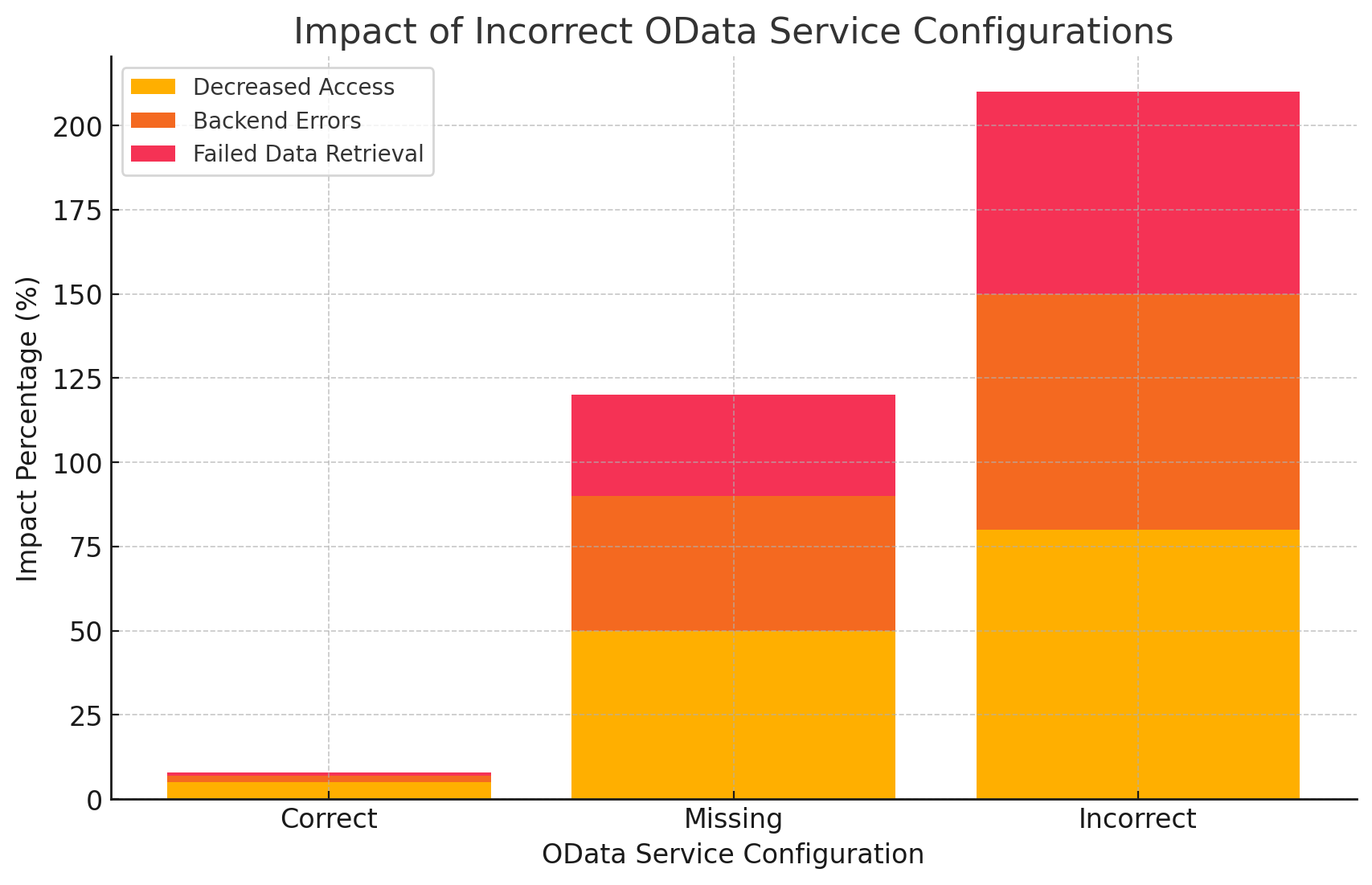
Impact of Incorrect OData Service Configurations
This stacked bar chart visualizes the impact of missing or incorrect OData services, with the breakdown of decreased access, backend errors, and failed data retrieval.
3. Incorrect Application of Fiori Launchpad Role Assignments
The Fiori Launchpad serves as the central hub for accessing Fiori applications. Authorization issues often occur when users cannot access the Launchpad or specific apps, even if their roles are correctly configured on the back end.
Key Issues:
- Launchpad Role Assignment: Sometimes, users have the necessary roles for individual apps but fail to gain access to the Launchpad due to missing roles or incorrect configurations.
- Catalogs and Groups: Fiori apps are grouped into catalogs and assigned to specific groups within the Launchpad. If users lack the proper catalogs or groups, they cannot access certain apps, even if their roles on the backend are correct.
Solution:
Ensure users are assigned the appropriate Fiori Launchpad roles, catalogs, and groups. The best practice is to assign roles such as SAP_FIORI_LAUNCHPAD_USER and maintain consistency between the Fiori Launchpad and backend systems.
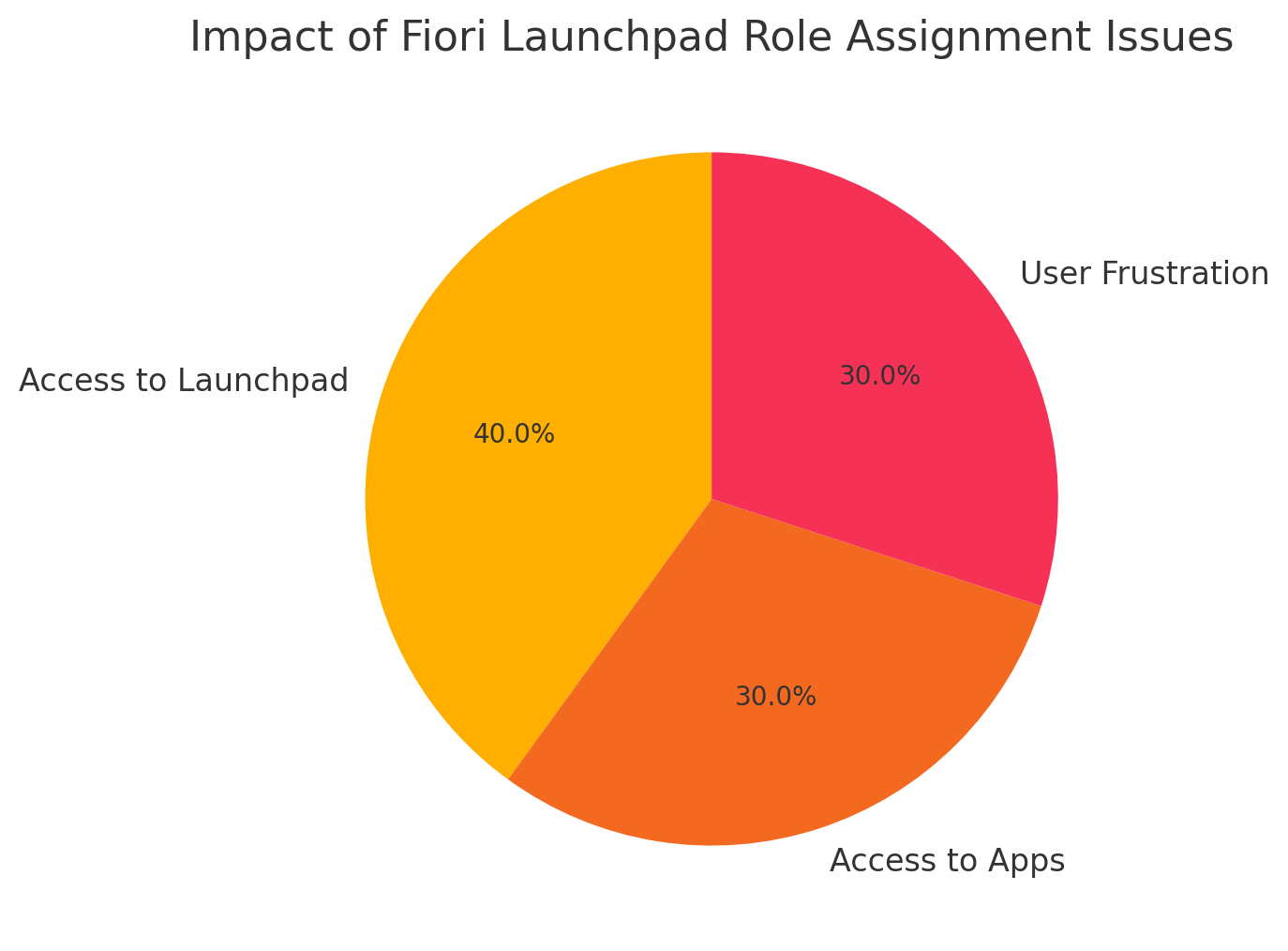
Impact of Fiori Launchpad Role Assignment Issues
The pie chart shows the proportion of issues caused by incorrect role assignments in the Fiori Launchpad, including access to the Launchpad, access to apps, and user frustration.
4. Authorization Issues in Custom Fiori Applications
Custom Fiori apps often present unique authorization challenges. These apps may have specific, business-critical functionality and customized authorization objects, making standard role assignments ineffective.
Key Issues:
- Custom Authorization Objects: Custom-built Fiori applications may rely on new or non-standard authorization objects. This can lead to access issues if those objects are not correctly included in roles.
- Custom Roles and Authorizations: Developers might create custom roles with specific restrictions that are not adequately tested or documented.
Solution:
Work closely with development teams to ensure custom authorization objects are correctly defined and included in the relevant roles. Use transaction SU53 to trace authorization errors and carefully review custom role configurations.
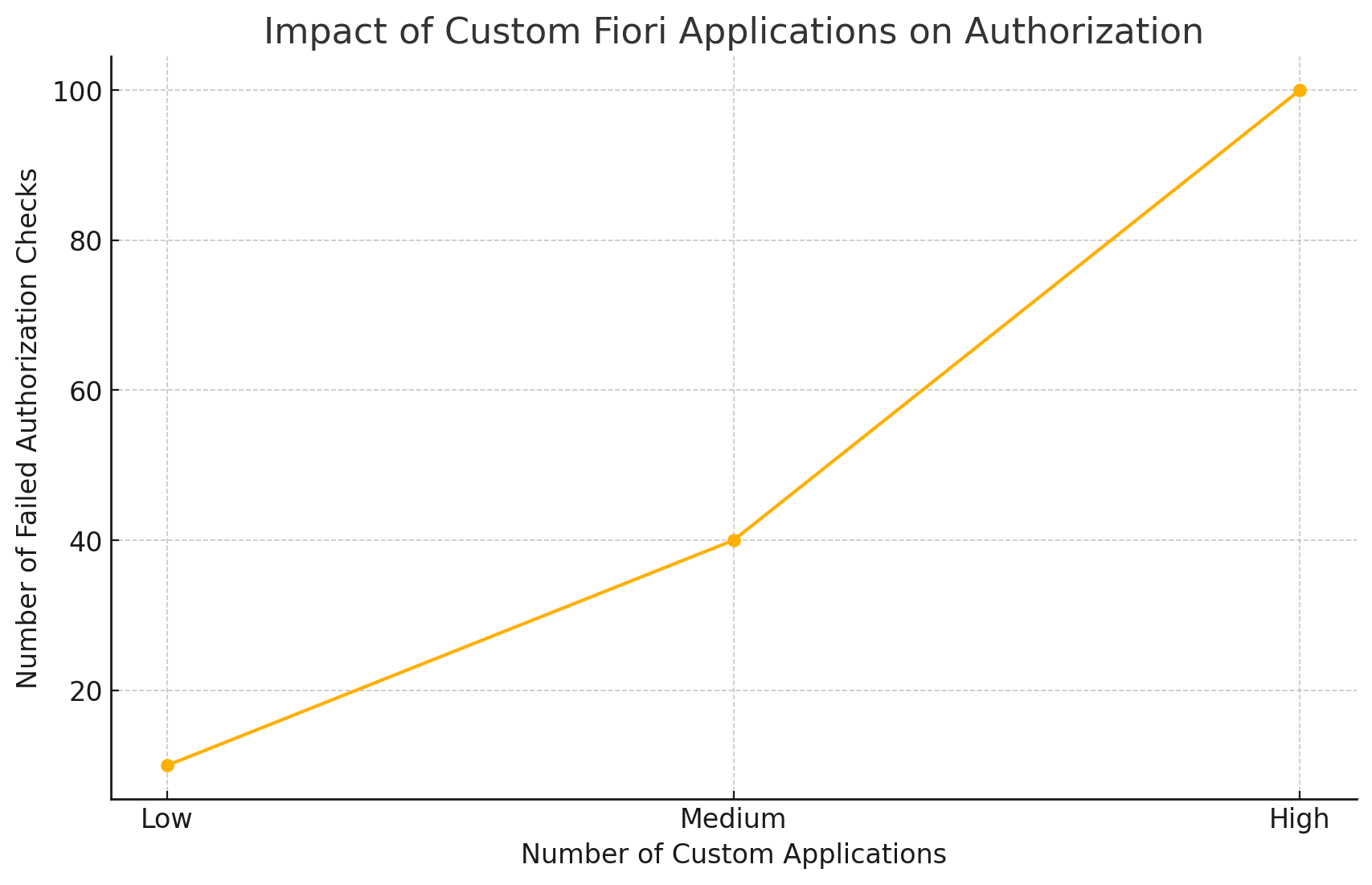
Impact of Custom Fiori Applications
This line chart tracks the trend of failed authorization checks as the number of custom Fiori applications increases, highlighting how customization leads to more authorization challenges.
5. Authorization Consistency Across Multiple Systems (Backend, Frontend, and SSO)
SAP S/4HANA landscapes are often spread across multiple systems, such as the backend SAP system, Fiori frontend server, and identity management solutions. Ensuring consistent and synchronized authorization across all these systems can be pretty challenging.
Key Issues:
- Cross-System Authorization Inconsistencies: Authorization issues can arise if roles and authorizations are not correctly synchronized across different systems.
- Single Sign-On (SSO) Configuration: In environments with SSO, incorrect or incomplete SSO configuration can result in users being unable to authenticate correctly, causing authorization failures.
- User Provisioning: If user roles and authorizations are not provisioned properly across systems, users might be denied entry to specific apps.
Solution:
Ensure a seamless flow of user information across all systems involved. Review SSO configurations and use tools like SAP Identity Management (IdM) to maintain consistency. Also, user access should be regularly tested across all connected systems to identify any potential gaps in authorization settings.
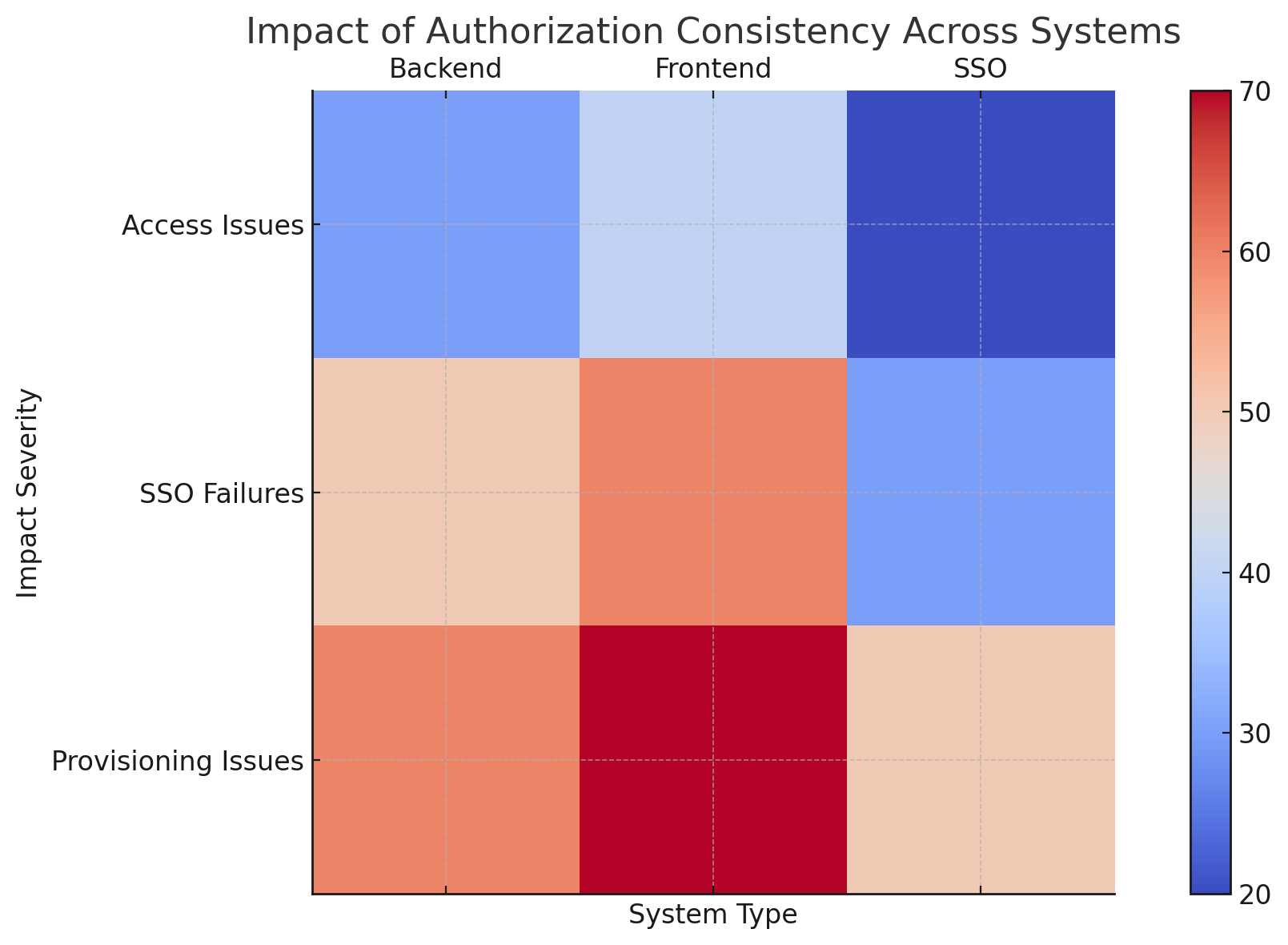
Impact of Authorization Consistency Across Systems
The heatmap represents the severity of access issues, SSO failures, and provisioning issues across different systems (Backend, Frontend, SSO), showing how inconsistencies affect overall authorization performance.